The AWS Secrets Manager secures, stores, and controls access to tokens, passwords, certificates, and other secrets in modern computing. The AWS Secrets Manager extension provides your pipeline with access to AWS secrets.
Please note this feature is disabled on Drone Cloud. This feature is only available when self-hosting.
AWS Secrets integration is provided by an extension and is only available if your system administrator has installed the extension.
Creating Secrets
Create a secret from the AWS console. In the below example we store the Docker username and password.
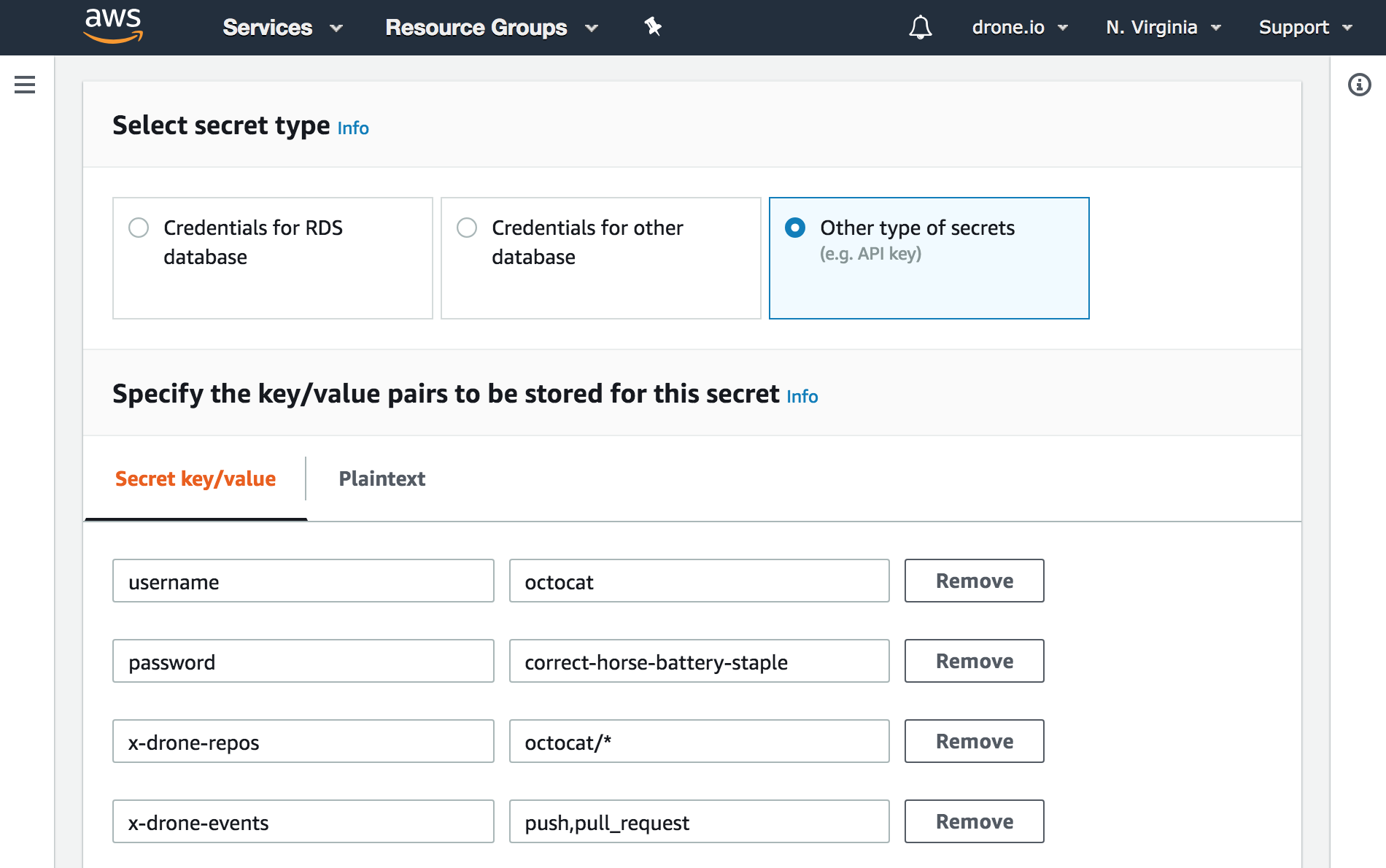
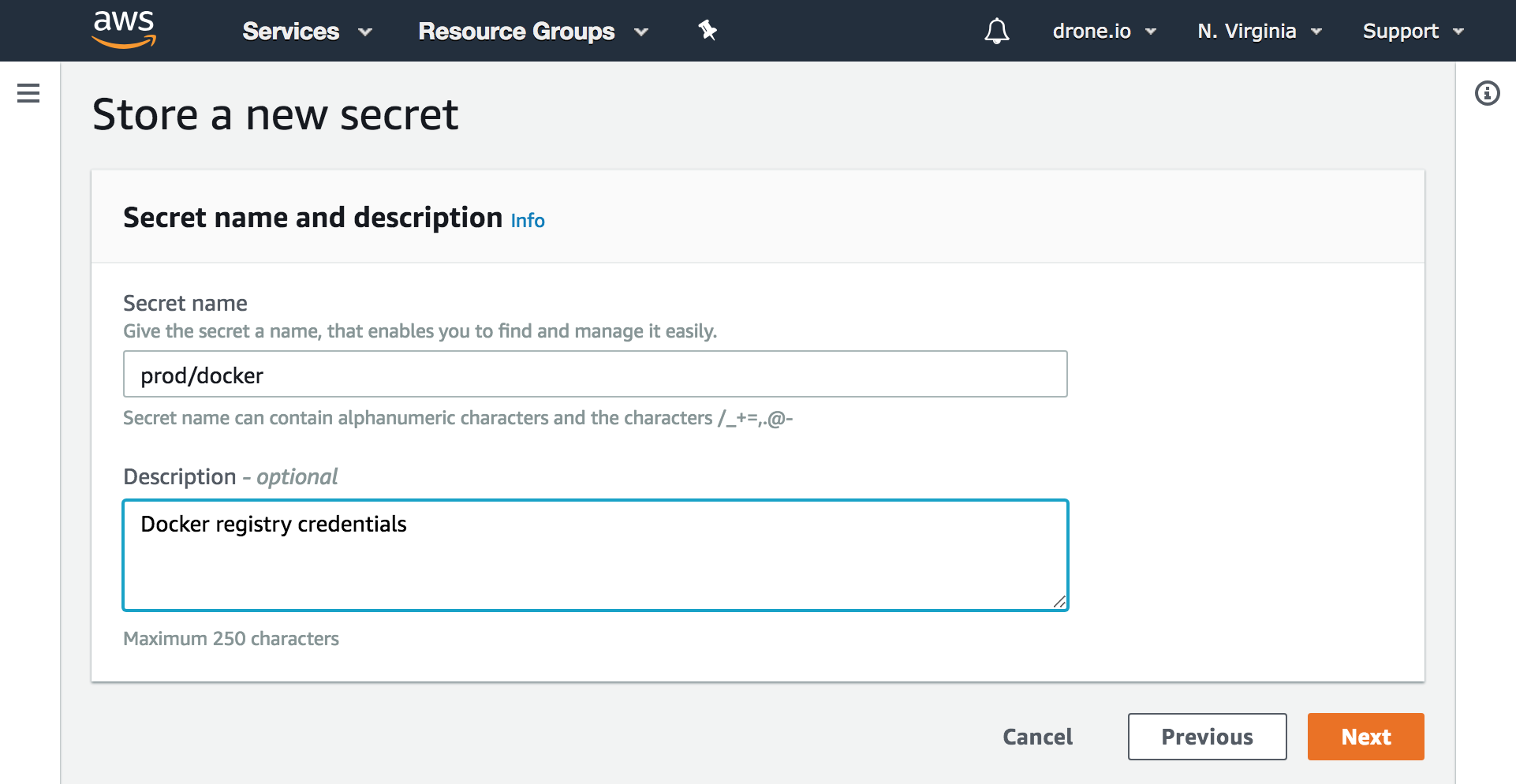
Accessing Secrets
Once our secrets are stored in AWS, we can update our yaml configuration file to request access to our secrets. First we define a secret resource in our yaml for each external secret. We include the path to the secret, and the name or key of value we want to retrieve:
|
|
We can then reference the named secrets in our pipeline:
|
|